Step-by-Step Guide- Setting Up PacketFence for Enterprise Network Access Control
Introduction
PacketFence is a powerful open-source Network Access Control (NAC) solution that provides robust security features for enterprise networks. It manages network access by enforcing authentication, authorization, and accounting while providing captive portal capabilities, BYOD registration, and network isolation for non-compliant devices. This comprehensive guide walks IT system engineers through the installation and configuration process, including setting up certificates, PKI integration, and Intune connectivity.
Initial Configuration
Accessing the Configurator
When you first boot up PacketFence, you'll be presented with a console interface. The default credentials are:
Username: root
Password: p@ck3tf3nc3
Changing the Root Password
For security reasons, change the default root password immediately:
# as root
passwd
# follow prompts to set a new password
Network Configuration
During initial setup, you'll need to configure your network settings. Make sure to properly configure your network adapter settings based on your environment requirements. PacketFence typically requires multiple network interfaces to separate management traffic from enforcement networks.
Tip: Plan your network segmentation carefully before configuring PacketFence. The solution works best when you have clearly defined management, registration, isolation, and production networks. The management interface should be connected to your secure management VLAN, while additional interfaces handle registration and isolation functions.
When configuring network interfaces, you'll need to assign static IP addresses to your management interface and determine which interfaces will handle PacketFence's enforcement mechanisms. The configurator will guide you through setting up:
- Management network (for administration)
- Registration network (for device onboarding)
- Isolation network (for quarantining non-compliant devices)
- Production networks (for normal network access)
Finishing Basic Setup
Complete the configurator by following the on-screen prompts. When asked about Fingerbank integration, you can skip this step as it's not required for basic functionality. Fingerbank provides device fingerprinting capabilities that enhance PacketFence's ability to identify device types, but this can be configured later.
Make sure to save all provided passwords during setup - you'll need them later! The configurator will generate several credentials for database access, admin portal, and various services that PacketFence uses internally.
After the initial configuration completes, you'll be able to access the PacketFence admin interface using the web browser. Login with the admin credentials provided during setup.
Setting Up Web Service Certificates
Using properly signed SSL certificates is crucial for a production PacketFence deployment. We'll implement a public signed wildcard certificate for the web server. This ensures that users connecting to the captive portal don't receive certificate warnings, which improves security perception and prevents users from developing the habit of ignoring certificate warnings.
Converting Certificate Formats
If you have a certificate in p12/pfx format, use these commands to extract the key components:
On macOS:
# extract unencrypted RSA private key
openssl pkcs12 -in bundle.p12 -nocerts -nodes | tee tmp.key | openssl pkcs8 -topk8 -nocrypt -in /dev/stdin -out server.key
# extract server cert (includes SANs)
openssl pkcs12 -in bundle.p12 -clcerts -nokeys -out server.crt
# cleanup
rm -f tmp.key
These commands extract the private key and certificate from a PKCS#12 bundle. The intermediate step using tmp.key ensures that the key is properly formatted for PacketFence's requirements. The resulting server.key file contains an unencrypted private key in PKCS#8 format, while server.crt contains your certificate including any Subject Alternative Names (SANs).
The private key string needs to start with -----BEGIN RSA PRIVATE KEY----- and end with the corresponding footer. Also, make sure the intermediate certificate is added, otherwise the portal service over port 443 won't be available.
Installing the Web Certificate
-
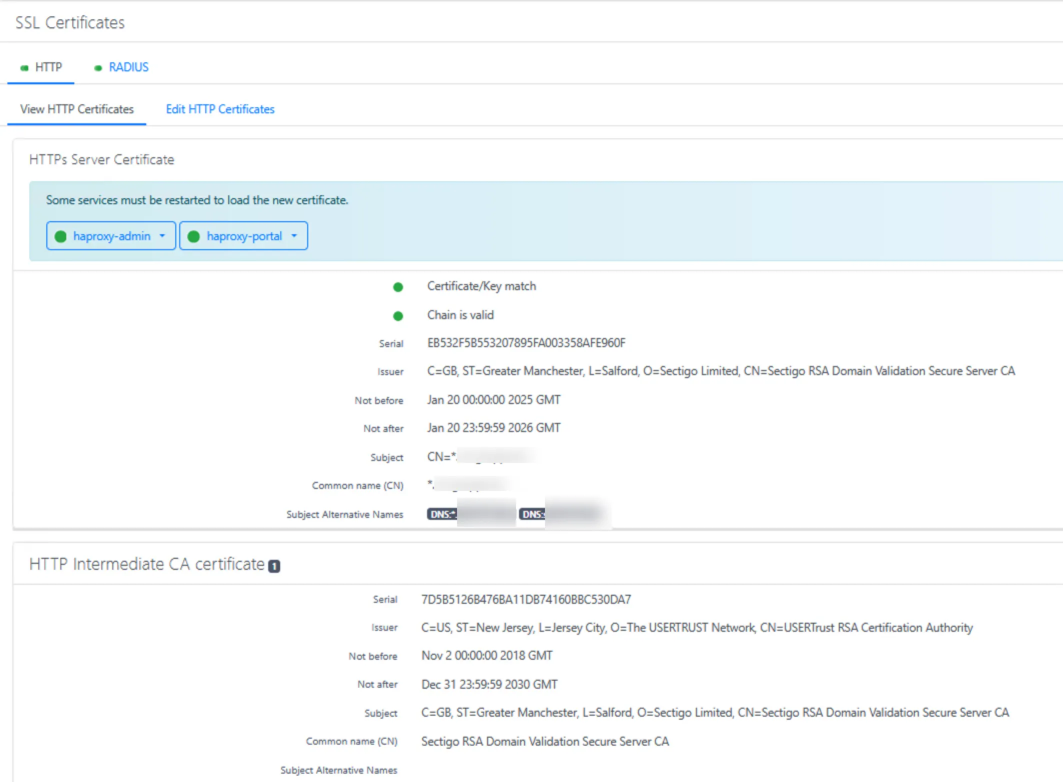
Navigate to System Configuration → SSL Certificates → Edit HTTP Certificates in the PacketFence admin portal
-
Replace HTTP Server Certificate with the content of server.crt - copy the full text including BEGIN and END CERTIFICATE lines
-
Optional: Deselect Find HTTPs Server intermediate CA(s) automatically and add your intermediate cert content manually. This ensures you have the exact certificate chain you want rather than relying on automatic discovery
-
Replace HTTP Server Private Key with the content of server.key - include the full text with BEGIN and END PRIVATE KEY lines
-
Click Save to apply changes
-
IMPORTANT: Restart services to make HTTP/80 available by clicking on the "Restart" button in the confirmation dialog
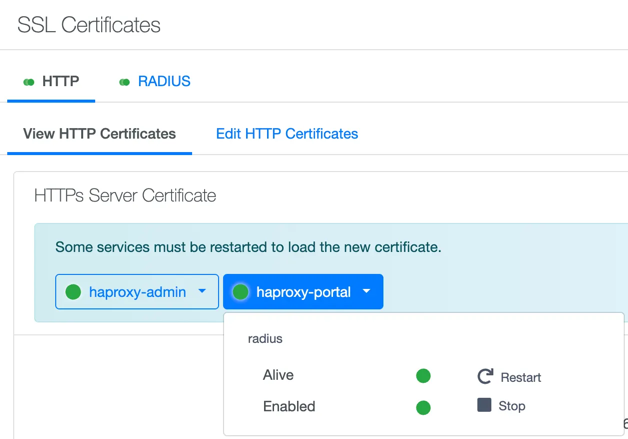
After making certificate changes, verify that both HTTP and HTTPS services are functioning correctly. Use browser tools to check certificate validity. If you access the management interface and see a valid HTTPS connection without warnings, your certificate installation was successful. Remember that the captive portal needs to work on both HTTP and HTTPS to handle various client redirections properly.
Setting Up PKI Infrastructure
PacketFence includes an integrated PKI (Public Key Infrastructure) that allows you to create and manage certificates. This is particularly useful for certificate-based authentication with 802.1X, which provides stronger security than password-based methods.
Creating a Certificate Authority
-
Navigate to the PKI section and select New Certificate Authority to establish a Certificate Authority that will sign all certificates used in your environment
-
Enter your organization's CA details and save. Include meaningful information in fields like Organization, Organizational Unit, and Common Name to identify your CA properly
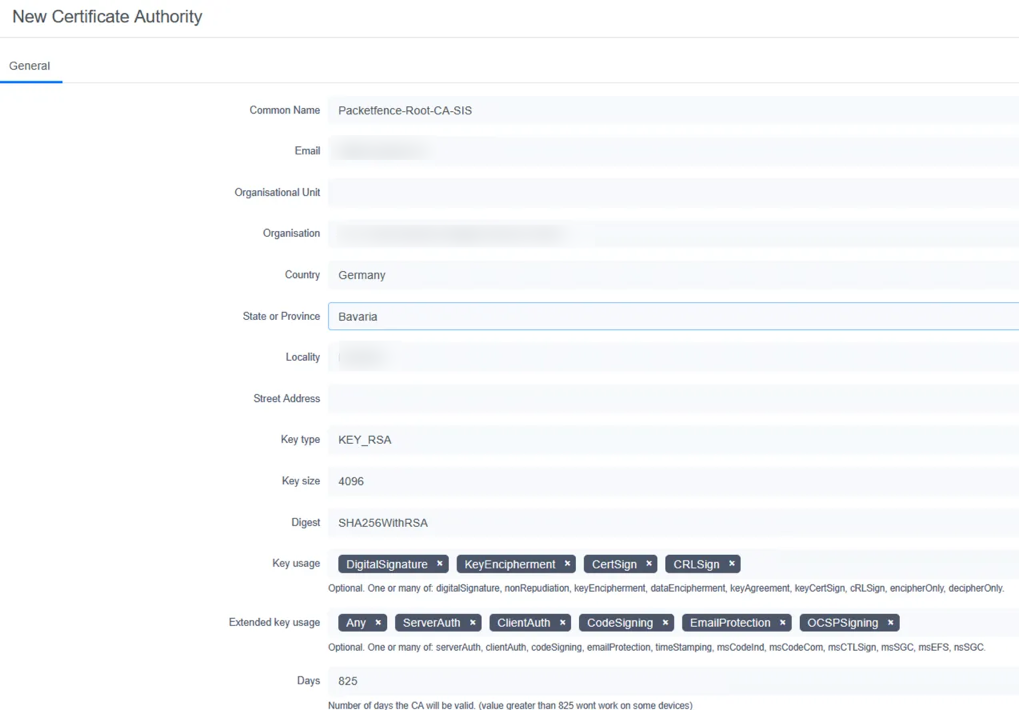
-
Copy and save the CA public cert as ca.crt - you'll need this file later for device configurations and RADIUS setup
The Certificate Authority is the foundation of your PKI. It's used to sign all certificates issued by PacketFence, and client devices must trust this CA for certificate-based authentication to work.
Configuring Microsoft Intune Integration
Before creating certificate templates, we need to set up Intune integration to enable automated certificate enrollment for mobile devices:
-
In Microsoft Entra ID (Azure AD), create a new app registration with appropriate permissions for device management
-
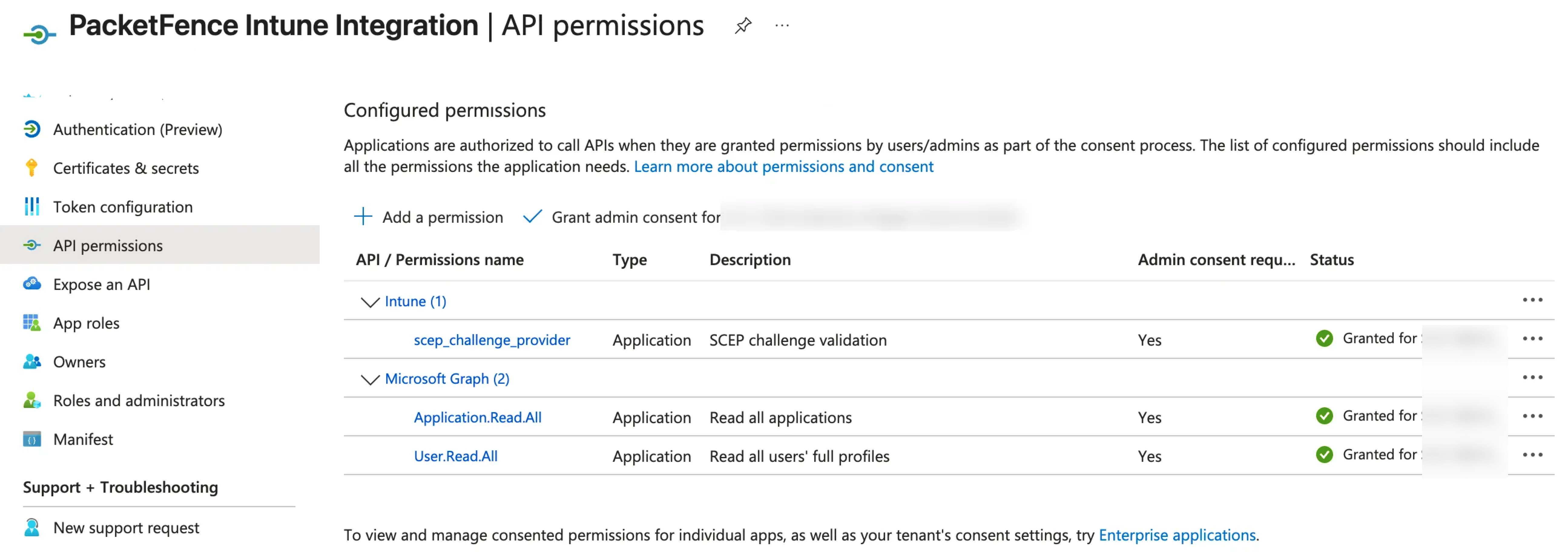
Add the following permissions to the app registration:
- DeviceManagementConfiguration.ReadWrite.All
- DeviceManagementManagedDevices.ReadWrite.All
- DeviceManagementServiceConfig.ReadWrite.All
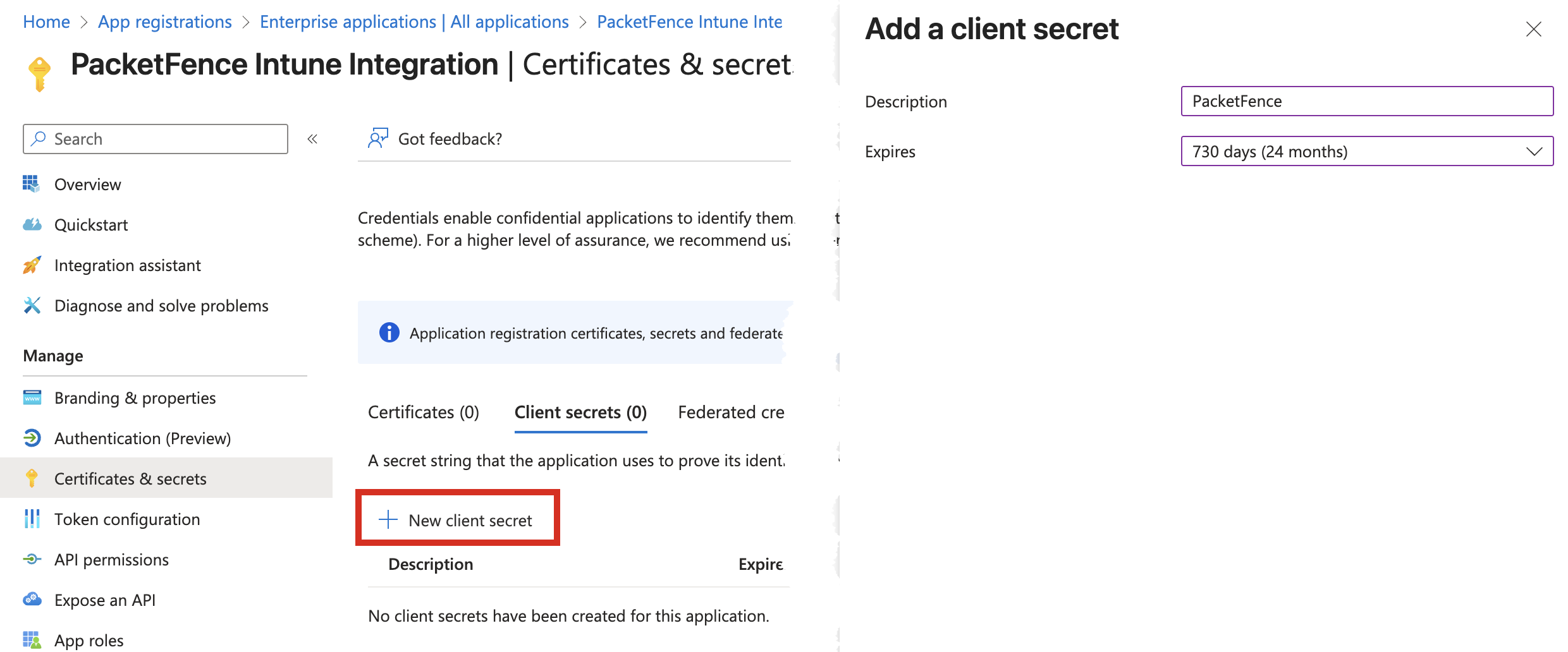
-
Create a client secret and copy its value - note that this secret will only be shown once during creation
-
In PacketFence, go to Configuration → Cloud Services → New Cloud Service → Intune
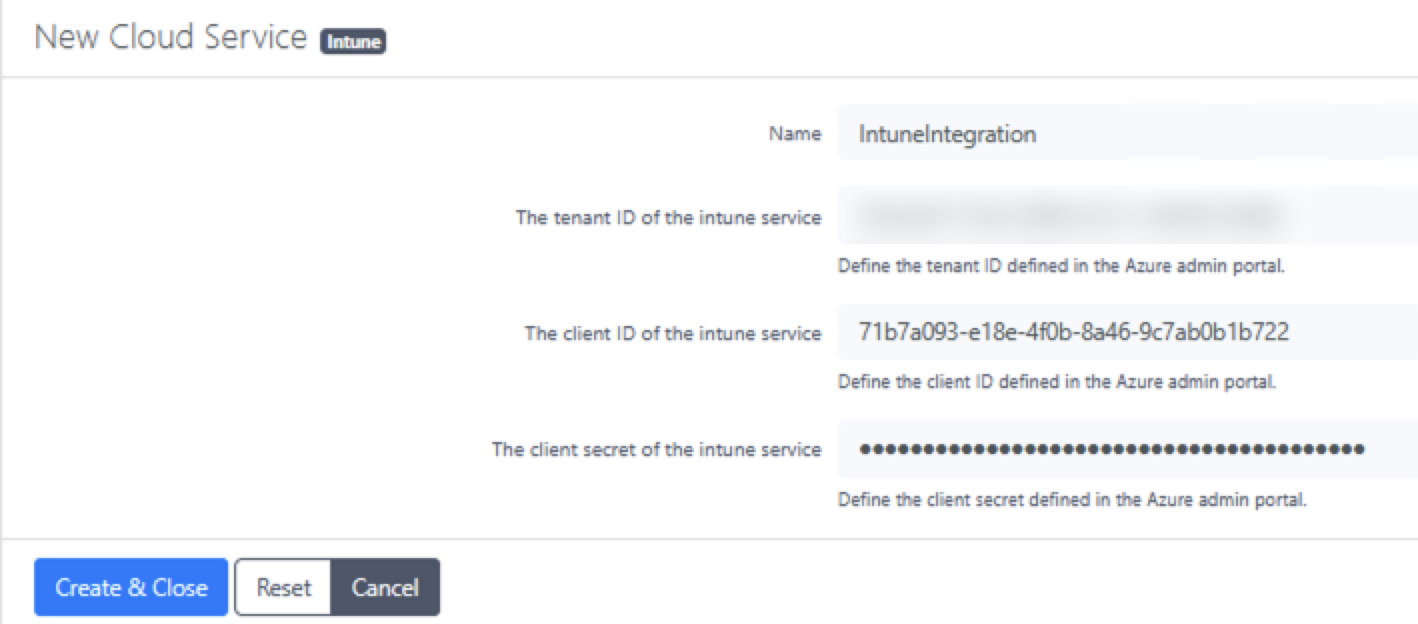
-
Enter a profile name, tenant ID, client ID, and the secret created in the previous step. These values connect PacketFence to your Microsoft Intune environment, allowing it to push certificate profiles to devices
This integration allows PacketFence to communicate with Intune for certificate management, enabling automated distribution of certificates to managed devices, which streamlines the enrollment process and reduces administrative overhead.
Creating Certificate Templates
We need to create two certificate templates with specific configurations:
1. RADIUS Server Certificate Template
- Maximum validity: 825 days (complies with industry standards for server certificates)
- Purpose: Used for the RADIUS Server authentication
- Key Usage: Digital Signature, Key Encipherment
- Extended Key Usage: Server Authentication
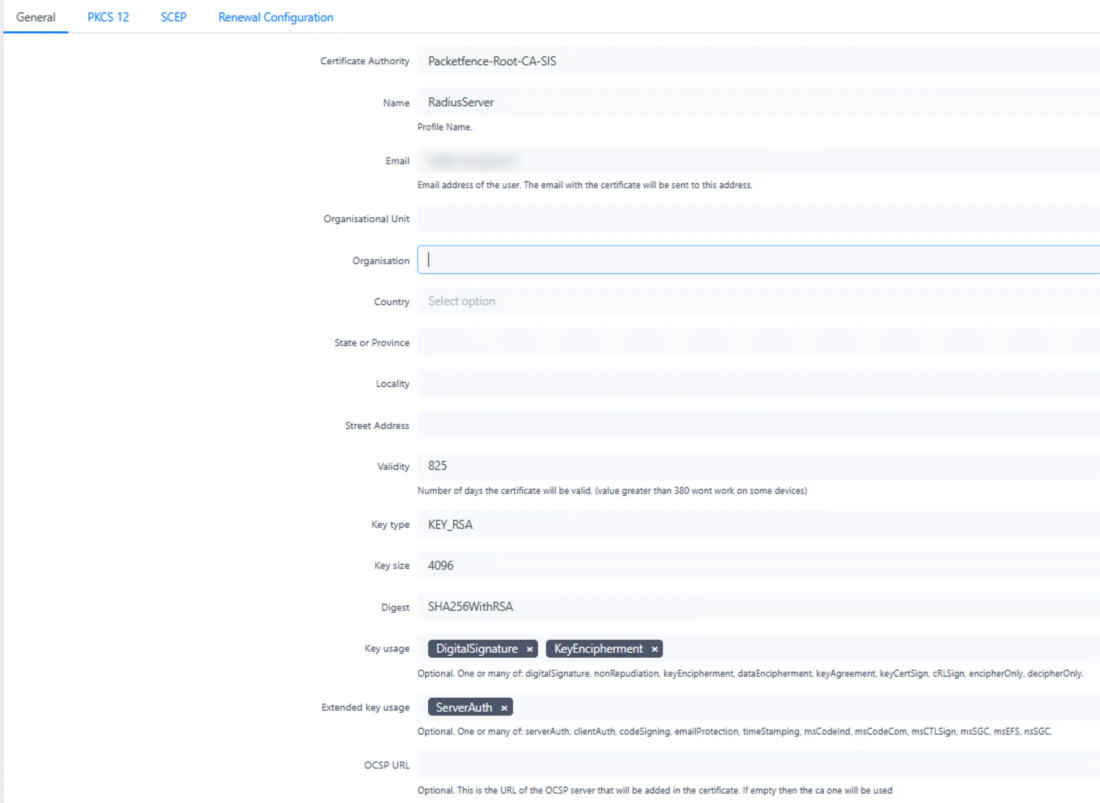
This template is used to generate the certificate that secures communications between wireless clients and the RADIUS server during 802.1X authentication.
2. User Certificate Template
-
Validity: 365 days (standard for user certificates to balance security and management overhead)
-
SCEP enabled (Simple Certificate Enrollment Protocol for automated deployment)
-
Cloud Intune Integration enabled (connects to the Intune profile created earlier)
-
Key Usage: Digital Signature
-
Extended Key Usage: Client Authentication
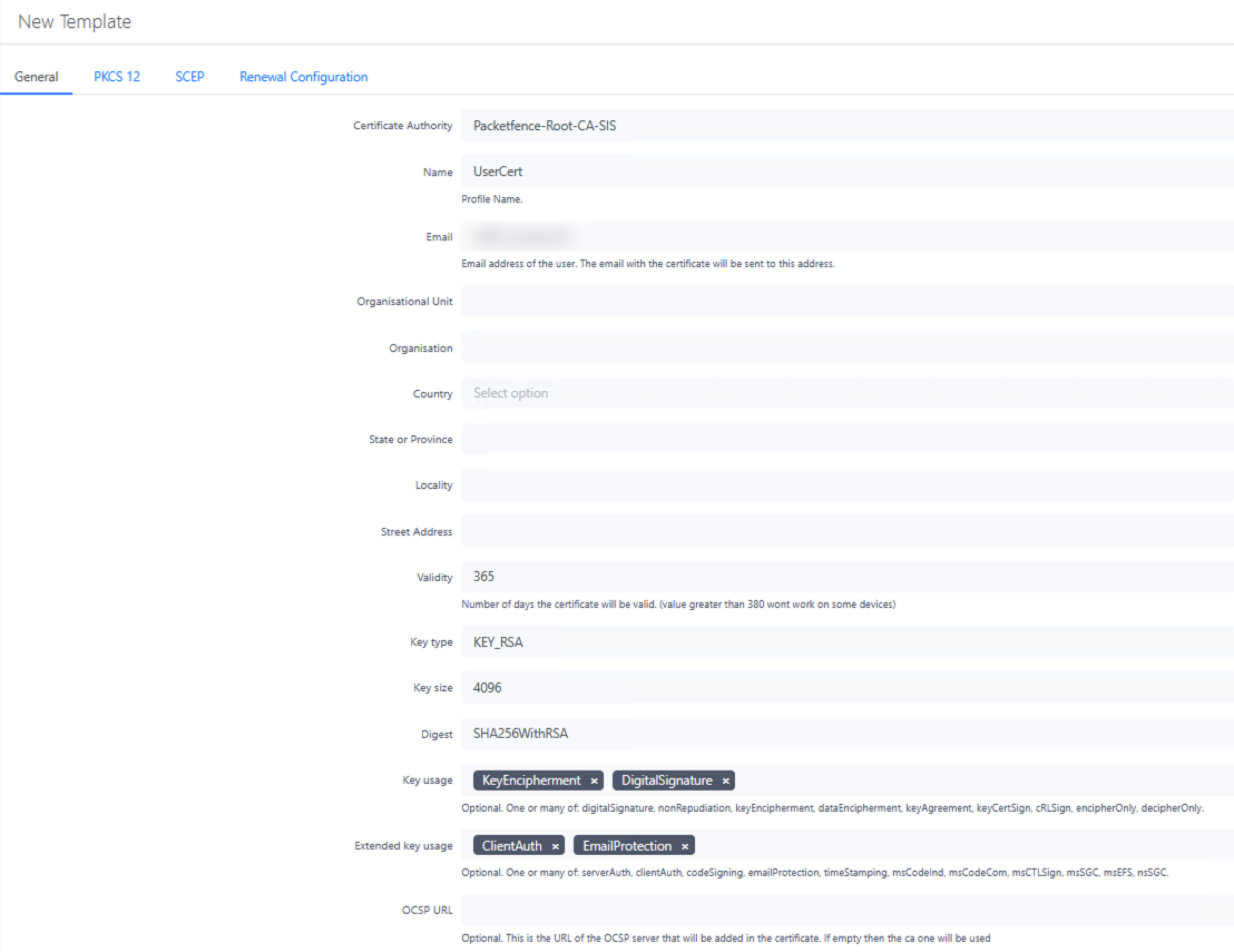
This template generates certificates for user authentication, enabling secure 802.1X connections without password prompts.
For the User Certificate template, make sure to:
-
Enable SCEP in the SCEP tab to allow automated certificate enrollment
-
Create a secure challenge password - this should be complex and randomly generated
-
Enable Cloud Integration and select your Intune profile to link certificate enrollment with your MDM solution

SCEP allows devices to request certificates automatically without manual intervention, while the Intune integration ensures that only managed devices can obtain certificates.
Creating and Installing RADIUS Server Certificate
For RADIUS to function properly, we need to create a certificate using the RADIUS Server template. This certificate secures the authentication process when clients connect to your network:
-
Go to Integration → PKI → Certificates → Certificates and create a new certificate with the RADIUS Server template
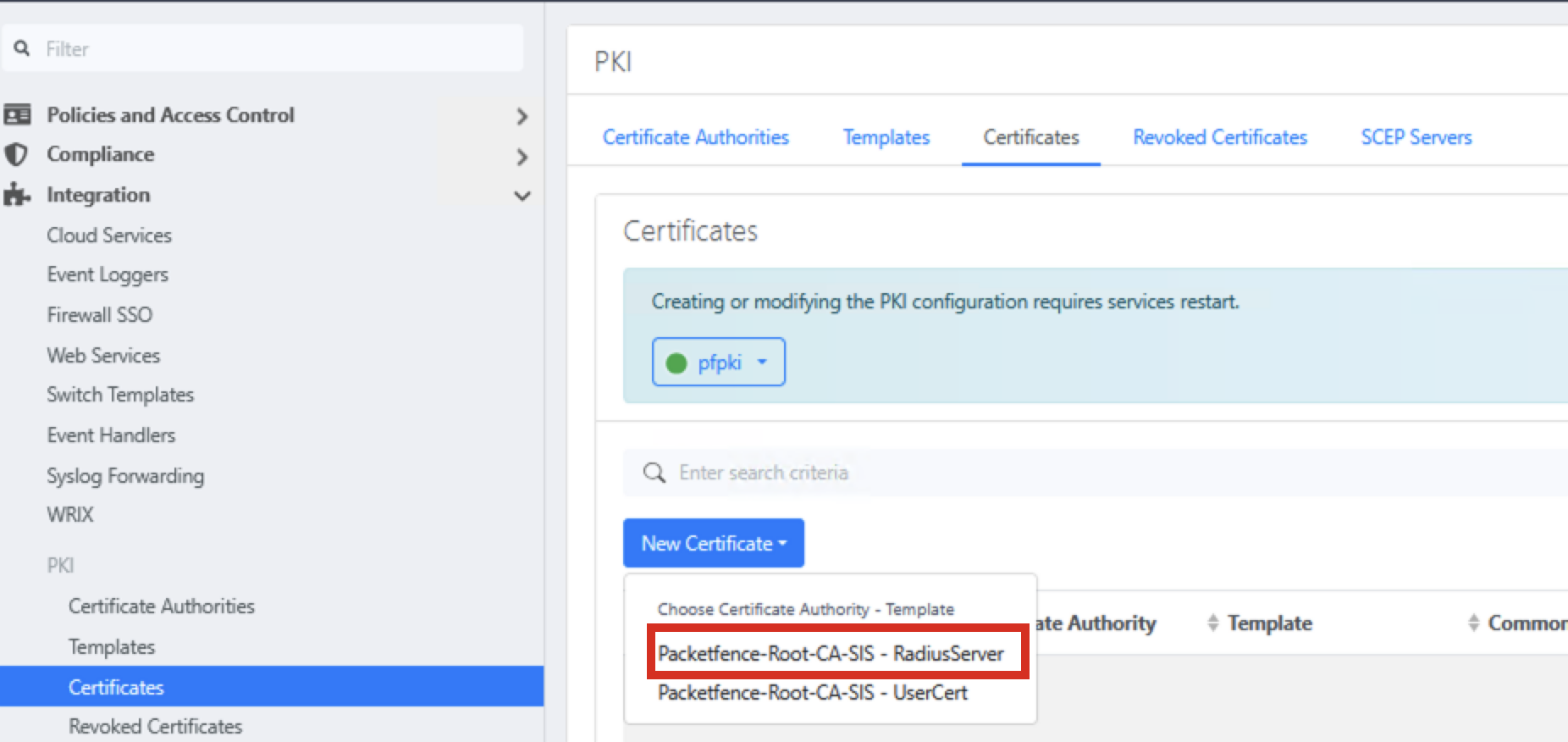
-
Enter certificate details, using the FQDN of your RADIUS server for both Common Name and DNS Names. This ensures that clients can verify the server's identity during authentication
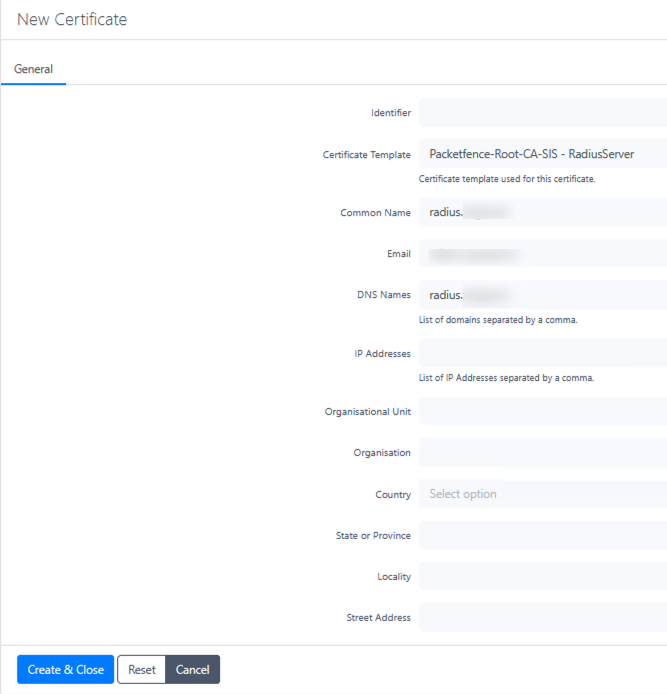
-
If your RADIUS server has multiple DNS names or IP addresses that clients might use to connect, include them all as Subject Alternative Names (SANs)
-
Download the certificate bundle after creation
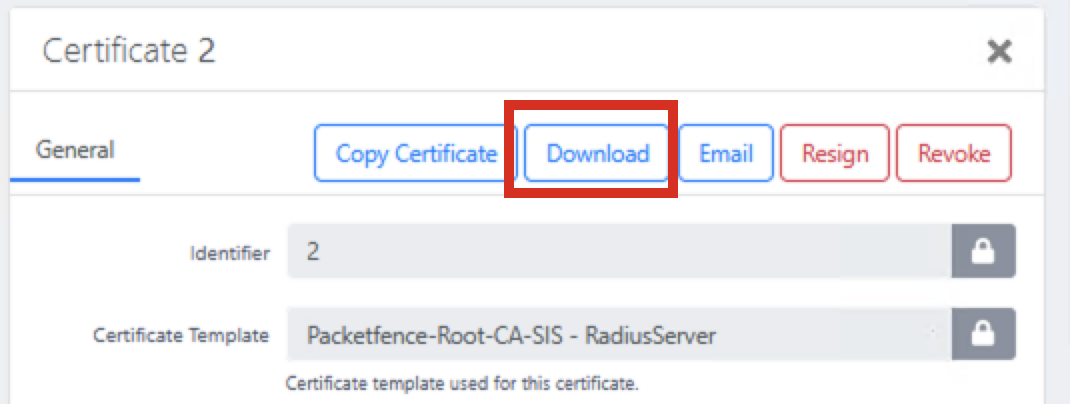
Note: The downloaded p12 file uses an older encryption format. When using OpenSSL to extract keys, you may need to add the -legacy parameter. Windows and macOS can generally import these files without issues. The p12 file contains both the certificate and private key in a password-protected format.
:::
Extract Certificate Components
On macOS, use these commands to extract the necessary files from the certificate bundle:
# extract unencrypted RSA private key
openssl pkcs12 -in bundle.p12 -nocerts -nodes -legacy | tee tmp.key | openssl pkcs8 -topk8 -nocrypt -in /dev/stdin -out server.key
# extract server cert (includes SANs)
openssl pkcs12 -in bundle.p12 -clcerts -nokeys -out server.crt -legacy
# cleanup
rm -f tmp.key
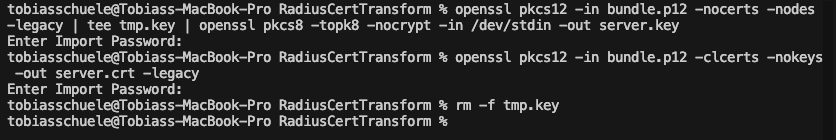
The -legacy parameter is needed because PacketFence uses an older encryption format in its PKCS#12 files. The extracted files include server.key (the private key) and server.crt (the public certificate).
Install the RADIUS Certificate
- Navigate to System Configuration → SSL Certificates → RADIUS → Edit RADIUS Certificate
- Replace RADIUS Server Certificate with the content of server.crt
- Replace RADIUS Server Private Key with the content of server.key
- Replace Certification Authority certificate with the content of ca.crt saved earlier
- Click Save and verify the certificate details are correct in the confirmation dialog
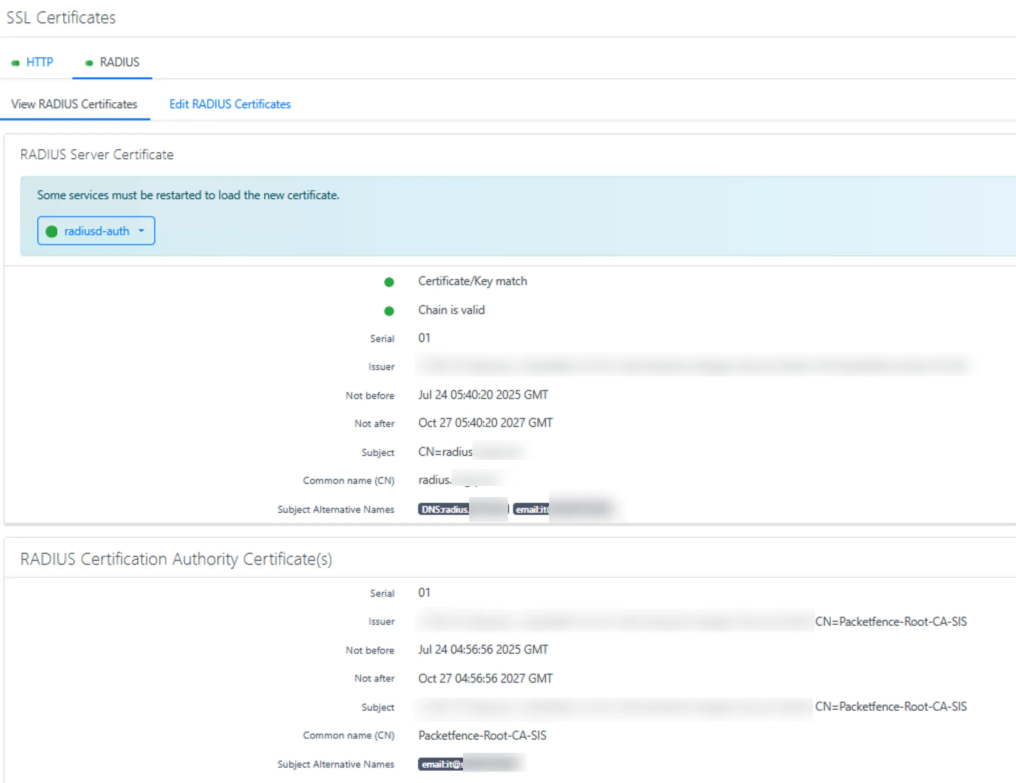
These steps configure the RADIUS server to use your custom certificate for all 802.1X authentication transactions. This is critical for secure wireless deployments as it allows clients to verify the identity of the RADIUS server before sending credentials.
Publishing SCEP for Mobile Device Management
To enable certificate enrollment for mobile devices, we need to publish the SCEP endpoint to the internet. This allows devices to request certificates regardless of their location. Microsoft Entra ID Application Proxy provides an easy method to accomplish this without exposing your entire PacketFence server.
For security purposes, only publish the specific SCEP endpoint rather than exposing the entire server to the internet. Using a path-based approach (/scep/) ensures that only the certificate enrollment functionality is accessible externally.
Setting Up Application Proxy
-
Go to the Entra ID admin portal Application Proxy section at https://entra.microsoft.com/#view/Microsoft_AAD_IAM/AppProxyOverviewBlade
-
Select Configure an app to create a new application proxy configuration
-
For the Internal URL:
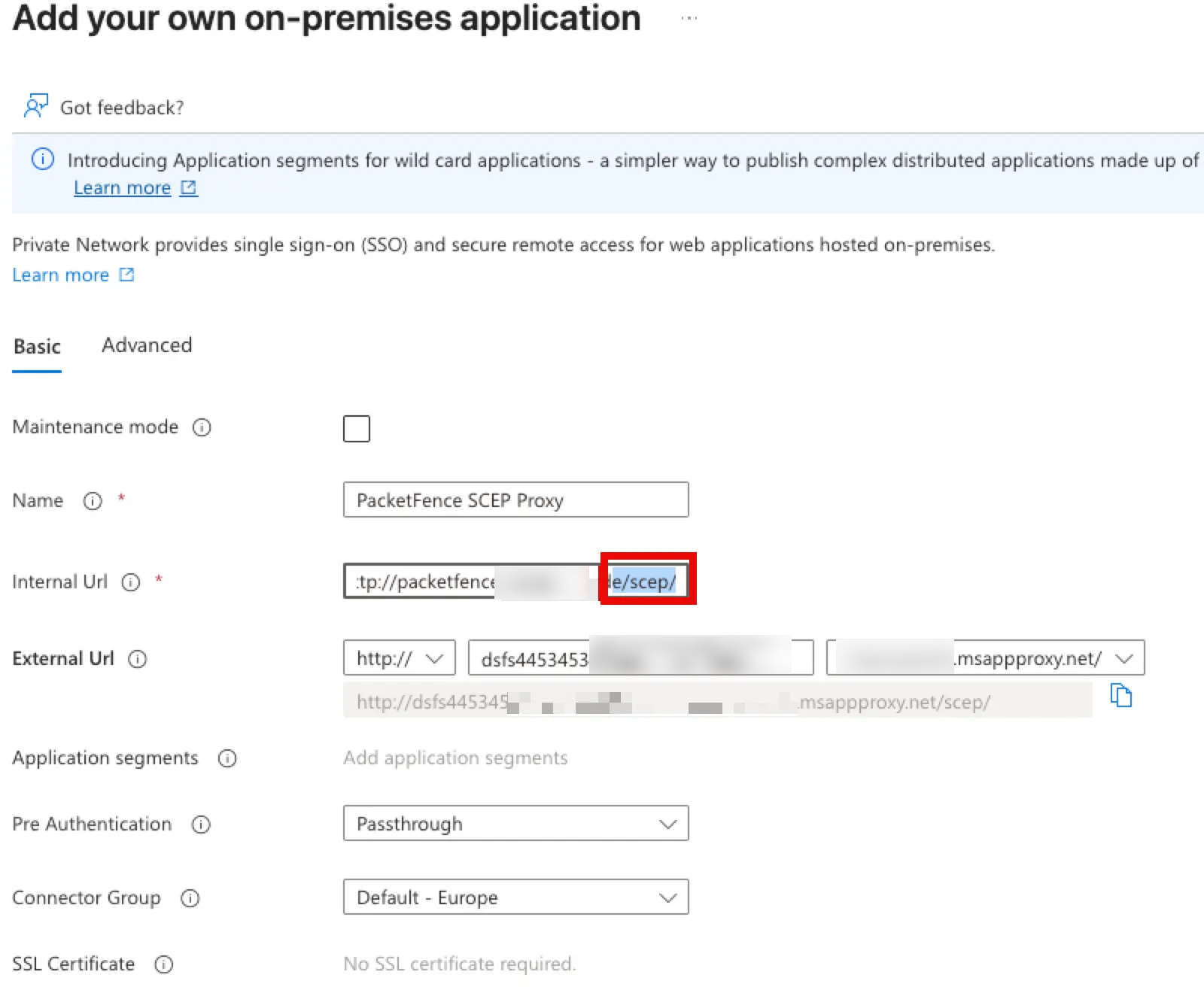
- Use HTTP (not HTTPS) - PacketFence's SCEP endpoint runs on HTTP
- Format should be: http://packetfence.yourdomain.com/scep/
- Add /scep/ to the FQDN for security (limit exposure to only the SCEP endpoint)
-
For the External URL:
- Use a random, hard-to-guess name for better security (e.g., scep-r4nd0m-n4m3)
- The default msappproxy.net domain can be used unless you have a custom domain configured
- Configure with HTTP (not HTTPS) to match the internal configuration
-
Set Pre-Authentication to Passthrough - this is critical as SCEP clients cannot handle interactive authentication
The Application Proxy creates a secure tunnel between your internal PacketFence server and the internet, allowing mobile devices to enroll for certificates while keeping your server protected.
Building and Using SSCEP for Testing
To test your SCEP configuration, you can build and use the SSCEP tool, which allows you to test certificate enrollment against your PacketFence SCEP server:
Building SSCEP on macOS
# 1) Xcode command-line tools (needed for clang & make)
xcode-select --install # one-time on a fresh Mac
# 2) Runtime & build deps
brew install autoconf automake libtool pkg-config openssl
# 3) Grab the source or use GitHub Desktop
git clone https://github.com/certnanny/sscep.git
cd sscep
# 4) Regenerate Autotools files
glibtoolize # GNU libtool on macOS is called 'glibtool'
aclocal
automake -a -c -f
autoreconf # wraps autoconf & friends
# 5) Configure — tell it where Homebrew puts OpenSSL
export PKG_CONFIG_PATH="$(brew --prefix openssl@1.1)/lib/pkgconfig"
./configure
# 6) Compile and install
make
sudo make install # installs to /usr/local/bin/sscep by default
Testing SCEP Enrollment
Once SSCEP is installed, you can test your SCEP configuration with these commands:
# Generate a new key pair and CSR
openssl req -newkey rsa:2048 -keyout PRIVATEKEY.key -out MYCSR.csr
# Get the CA certificate
sscep getca -u http://[your-app-proxy-url]/scep/UserCert -c ca.crt
# Attempt to enroll with the SCEP server
sscep enroll -c ./ca-prefix -k ./private.key -r ./MYCSR.csr -u http://[your-packetfence-server]/scep/UserCert -l cert.crt -d -v
This testing process helps verify that your SCEP endpoint is correctly configured and can issue certificates before deploying to actual devices.
Intune Configuration
With the SCEP endpoint published, we now need to configure Microsoft Intune to distribute the CA certificate and SCEP profile to managed devices.
Installing the CA Certificate
All devices must have the root CA certificate installed as trusted for authentication and SCEP enrollment to work. Create policies in Intune for each platform:
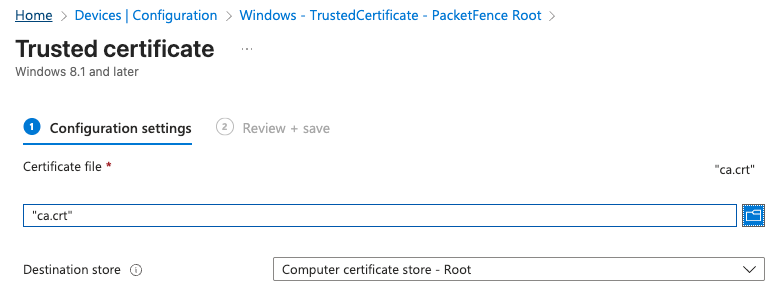
Windows Devices
Create a Trusted Certificate profile using the ca.crt file:
- Navigate to Devices > Configuration profiles > Create profile
- Platform: Windows 10 and later
- Profile type: Templates > Trusted certificate
- Certificate file: Upload the ca.crt file
- Certificate destination: Computer certificate store - Root
- Target this profile to appropriate device groups
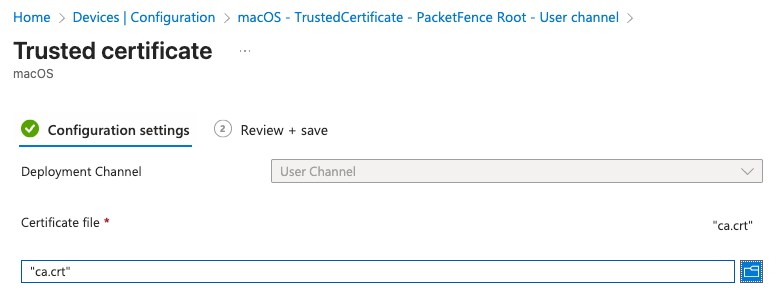
macOS Devices
Create separate policies for User and Device certificates if you plan to use both authentication methods:
- Navigate to Devices > Configuration profiles > Create profile
- Platform: macOS
- Profile type: Templates > Trusted certificate
- Certificate file: Upload the ca.crt file
- Create two profiles - one for User certificate store and one for System certificate store
- Target these profiles to appropriate device groups
If you want to use User and Device certificates for authentication, you need to install the device certificate in both User and Device certificate stores using separate policies.
iOS Devices
Create a Trusted Certificate profile specifically configured for iOS:
- Navigate to Devices > Configuration profiles > Create profile
- Platform: iOS/iPadOS
- Profile type: Templates > Trusted certificate
- Certificate file: Upload the ca.crt file
- Target this profile to appropriate device groups
Creating SCEP Profiles
Create SCEP certificate profiles for each platform, using your published SCEP URL. Replace the placeholder with your actual URL:
http://[your-unique-name].msappproxy.net/scep/UserCert
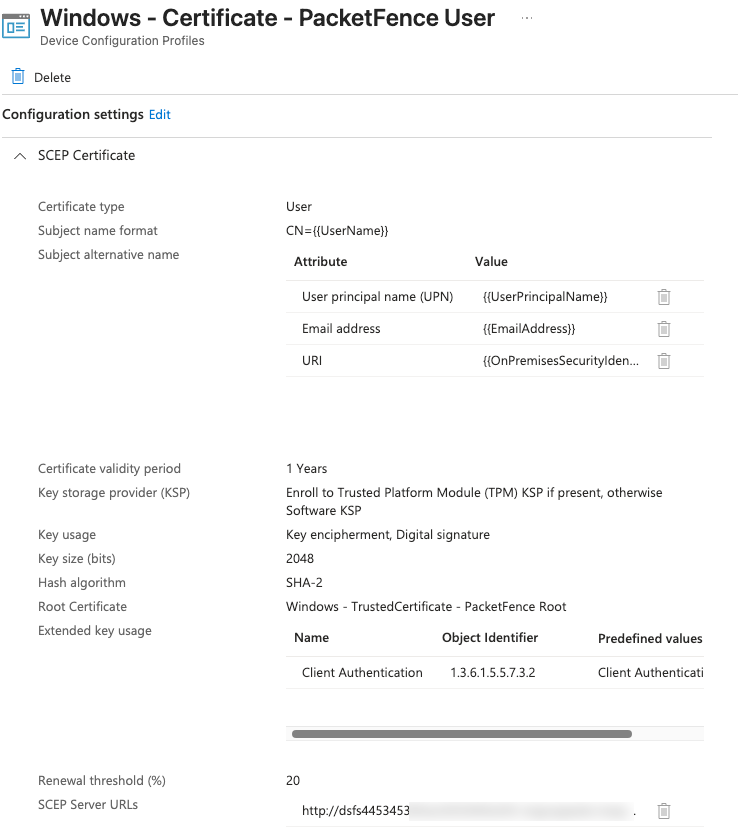
For Windows devices, configure a SCEP certificate profile with:
-
Certificate type: User
-
Subject name format: Common name as email or UPN
-
Certificate validity period: 1 year
-
Key usage: Digital signature
-
Extended key usage: Client Authentication
-
SCEP Server URLs: Your published SCEP URL
Similar configurations should be created for macOS and iOS devices, adjusting platform-specific settings as needed. Each platform requires its own SCEP profile tailored to the operating system's certificate handling capabilities.
Configure appropriate certificate settings for each platform (Windows, macOS, and iOS) according to your security requirements. Remember to target these profiles to the same groups that received the trusted certificate profiles.
Configuring RADIUS Clients
The final step is to configure your network devices (switches, wireless controllers, access points) as RADIUS clients. These devices will forward authentication requests to PacketFence for validation.
PacketFence provides detailed documentation for dozens of vendors at: https://www.packetfence.org/doc/PacketFence_Network_Devices_Configuration_Guide.html
In PacketFence, you'll need to define each network device as a RADIUS client:
- Navigate to Configuration > Policies and Access Control > Network Devices
- Add each switch or wireless controller, specifying its IP address and RADIUS shared secret
- Configure appropriate roles and access policies based on your security requirements
Example: Configuring an Ubiquiti Wireless Controller
Follow these general steps to configure an Ubiquiti Controller:
- Access your Ubiquiti Controller management interface
- Navigate to the Settings > RADIUS section
- Add a new RADIUS server using your PacketFence server's IP address
- Configure the shared secret (must match exactly what you set in PacketFence)
- Set authentication ports (typically 1812 for authentication, 1813 for accounting)
- Under the Wireless Networks section, edit each SSID that will use 802.1X
- Set Security to "WPA Enterprise" and select your RADIUS profile
- Apply and test the configuration by attempting to connect with a properly configured client
Once configured, the wireless controller will forward all authentication requests to PacketFence, which will validate certificates and provide access decisions based on your security policies.
Testing 802.1X Authentication
Before deploying to your entire network, it's critical to test your 802.1X authentication setup to ensure it's working correctly. The eapol_test utility is an excellent tool for this purpose as it allows you to simulate client authentication without actual hardware.
Using eapol_test.exe for Authentication Testing
The eapol_test utility can be found in the FreeRADIUS project and is available for Windows as eapol_test.exe. This tool simulates a client attempting to authenticate via 802.1X using various EAP methods.
You can download eapol_test from the following repository: https://github.com/janetuk/eapol_test
Creating Test Configuration Files
Before running tests, create configuration files for each authentication method you want to test. Here are examples for the most common scenarios:
1. Certificate-Based Authentication (EAP-TLS)
Create a file named eapol.conf with the following content:
network={
ssid="[NETWORK_NAME]"
key_mgmt=WPA-EAP
eap=TLS
identity="[IDENTITY]" # CN or UPN in client certificate
ca_cert="[CA_CERT_PATH]" # Root (and optionally intermediate) CA
private_key="[PRIVATE_KEY_PATH]" # Client certificate + key in PKCS#12 format
private_key_passwd="[PASSWORD]" # Password set during certificate export
}
2. Username/Password Authentication with AD (PEAP-MSCHAPv2)
Create a file named eapolPEAP.conf with the following content:
network={
ssid="[NETWORK_NAME]"
key_mgmt=WPA-EAP
eap=PEAP
identity="[USERNAME]"
password="[PASSWORD]"
ca_cert="[CA_CERT_PATH]"
phase2="auth=MSCHAPV2"
}
Running Authentication Tests
With your configuration files prepared, you can now run tests against your PacketFence RADIUS server. Use the IP address of your RADIUS server (not hostname) and the shared secret configured for your test client:
# Test EAP-TLS certificate authentication
eapol_test -a [RADIUS IP ADDRESS] -p 1812 -s [PASSPHRASE] -M 00:11:22:33:44:55 -c eapol.conf
# Test PEAP-MSCHAPv2 username/password authentication
eapol_test -a [RADIUS IP ADDRESS] -p 1812 -s [PASSPHRASE] -M 00:11:22:33:44:55 -c eapolPEAP.conf
Parameter explanation:
- -a: RADIUS server IP address
- -p: RADIUS server port (typically 1812)
- -s: Shared secret configured in PacketFence for this test client
- -M: Simulated MAC address of the client device
- -c: Path to configuration file
Analyzing Test Results
A successful authentication will show "SUCCESS" in the output, while failures will show error messages that can help diagnose issues. If authentication fails, check the following:
- Verify the RADIUS server is properly configured and running
- Ensure the client certificate is valid and trusted by the CA
- Check that the CA certificate is correctly installed on the RADIUS server
- Confirm that the shared secret matches between eapol_test and PacketFence
- For AD authentication, verify that the credentials are correct and the AD integration is working
For more detailed debugging, you can view the RADIUS server logs during testing:
sudo raddebug -t 300 -f /usr/local/pf/var/run/radiusd.sock
This command shows real-time authentication attempts and can be extremely helpful for troubleshooting complex authentication issues.
When reviewing logs, you may see some warning messages about "No EAP types configured". These can safely be ignored as they are not errors, but rather informational messages from the RADIUS server.
Troubleshooting
MySQL Database Permissions
If you encounter errors related to database access, ensure the MySQL user has appropriate permissions:
mysql -u root -p # or sudo mysql
GRANT ALL PRIVILEGES ON pf.* TO 'pf'@'localhost';
FLUSH PRIVILEGES;
Detailed RADIUS Logging
To view detailed logs from the RADIUS server for troubleshooting authentication issues:
sudo raddebug -t 300 -f /usr/local/pf/var/run/radiusd.sock
This command shows real-time RADIUS authentication attempts, helping diagnose certificate or configuration problems.
Database Configuration
If you need to change the database password or check the current configuration:
# Change MySQL password
ALTER USER 'pf'@'localhost' IDENTIFIED BY 'new_secure_password';
FLUSH PRIVILEGES;
# Update grants if needed
GRANT SELECT,INSERT,UPDATE,DELETE,EXECUTE,LOCK TABLES ON pf.* TO pf@'%' IDENTIFIED BY 'new_secure_password';
GRANT SELECT,INSERT,UPDATE,DELETE,EXECUTE,LOCK TABLES ON pf.* TO pf@'localhost' IDENTIFIED BY 'new_secure_password';
FLUSH PRIVILEGES;
# View database configuration
/usr/local/pf/bin/pfcmd pfconfig show resource::Database
# Reload configuration
/usr/local/pf/bin/pfcmd configreload hard
# Restart PacketFence services
sudo /usr/local/pf/bin/pfcmd service pf restart
After changing the database password, you'll need to reconfigure any secrets for integrated services like Entra ID App integration.
Conclusion
You have now successfully set up PacketFence as a Network Access Control solution with PKI integration and Intune connectivity. This powerful setup allows for certificate-based authentication and secure device management across your enterprise network.
This configuration provides several key benefits:
- Certificate-based authentication eliminates password-related vulnerabilities
- Automated certificate deployment reduces administrative overhead
- Integration with Intune ensures only managed devices receive certificates
- Centralized policy enforcement improves security posture
Remember to regularly backup your PacketFence configuration and update the system to maintain security and access to the latest features. Consider implementing regular certificate rotation schedules and monitoring for any authentication failures that might indicate configuration issues.
For ongoing management, familiarize yourself with PacketFence's reporting capabilities to monitor authentication trends and identify potential security incidents.